The University of Bío Bío in Santiago partnered with Nisum Chile to create a curriculum enrichment initiative for its technology track. Along with creating new classes, UBB students participated in an internship program and worked on their graduating thesis at Nisum Chile. This paper will review one of their projects, Kontun, a recommendation framework that helps compare and select single and multi-factor authentication methods.
As technology advances, software applications have progressively become more complex and able to hold larger and larger amounts of data. From initially being used solely for solving mathematical problems, computers are now used in a variety of tasks from creating artificial intelligence to calling a taxi cab. This white paper will cover how developers tackle authentication in their applications from bank transactions to holding sensitive medical data.
When a person tries to access their personal information, such as their social network, email, or bank accounts, it is common to first be required to input two pieces of information: the first would be a string that represents them, such as a username,
an identification number or their email address, and the second is a secret string, known as a password. The process above is known as authentication and it allows the applications to verify that the user trying to access the information is allowed to see it.
However, authentication with a password is not as secure as one would expect. In
the same way that technologies have evolved through time, so have the methods used for illegally accessing other people’s information. There is phishing, where a malicious person applies social engineering to obtain hints of people’s authentication information by speaking with them. Additionally, people often assign easy-to-remember strings such as their own names or their birthdays, making their accounts easier for those with malicious intent to access. Although there are ways to alleviate this, the more restrictions placed on the construction of passwords, the harder it is
for the user. Malicious people take advantage of this and use replay attacks, which automatically input thousands of string combinations until the user’s password is found. The above is even more complicated for Personal Identification Numbers (PIN), a variation of passwords that are used with ATMs and mobile phones. They are usually limited to a small number of digits composed solely of numbers.
There are multiple alternatives to the common username and password authentication methods such as the tokens usually used for performing online bank transactions or user biometrics (face recognition or fingerprints). However, all existing authentication methods are lacking in some aspects, such as some are not user-friendly, others are not adequately secure, and others are too expensive to implement or maintain over time. On the other hand, not all applications need as much security as others, or to be as useable as others; this depends on multiple features such as the information the application will hold (if it is sensitive or not), the users for which it is aimed, and the target context.
When developers work on new software applications that require the use of an authentication method, they have to consider the distinct features and restrictions of these applications to correctly select the best authentication method for them. However, this is more challenging for bigger applications where multiple criteria must be considered. Additionally, developers sometimes decide to simply implement the authentication methods that they have heard of most or are most familiar with, even if they are not the best option for the current application, due to their lack of knowledge of other authentication methods. It is important for developers to be knowledgeable on all methods in order to properly select the best authentication method for their applications.
Through this white paper, Nisum aims to share knowledge on different authentication methods, especially those that are usually not as widely known by software developers. We will discuss a variety of existing frameworks that help developers perform their comparison and selection of authentication methods for their applications.
Nisum is a global consulting firm that specializes in digital transformation for leading brands. Founded in 2000 with the customer-centric motto “Building Success Together,” they have grown to 3 continents by consistently enabling modernization for Fortune 500 brands. This work has been performed by Nisum Chile SPA, Nisum’s branch in Chile, in collaboration with the University of Bío-Bío.
Some Insight on Authentication Methods
Authentication methods can be categorized by authentication factors. There are three well-known authentication factors. These are:
-
Knowledge-based authentication, or “something that you know .” Text passwords and their lesser-known variant, graphical passwords, belong to this category.
-
Possession-based authentication, or “something that you possess .” All kinds of tokens can be found in this category, such as smart cards and mobile authentication.
-
Inherence-based authentication, or “something that you are .” Biometrics (metrics related to human features) is comprised of this category. Examples of biometrics are face recognition, fingerprints, and even human behavior.
It is possible to combine two or more authentication methods belonging to different factors in order to increase an application’s security even more. This is known as multi-factor authentication and will be addressed in more detail in the following paragraphs. Next, let us dive deeper into the authentication methods mentioned above, especially those less known by software developers.
Graphical Passwords
Graphical passwords are a variant of text-based passwords. As the name implies, these passwords are based on the use of images. This authentication method aims to solve some of the text passwords’ weaknesses, namely, the difficulty for users to memorize their passwords, as humans are able to remember images better than alphanumeric characters.
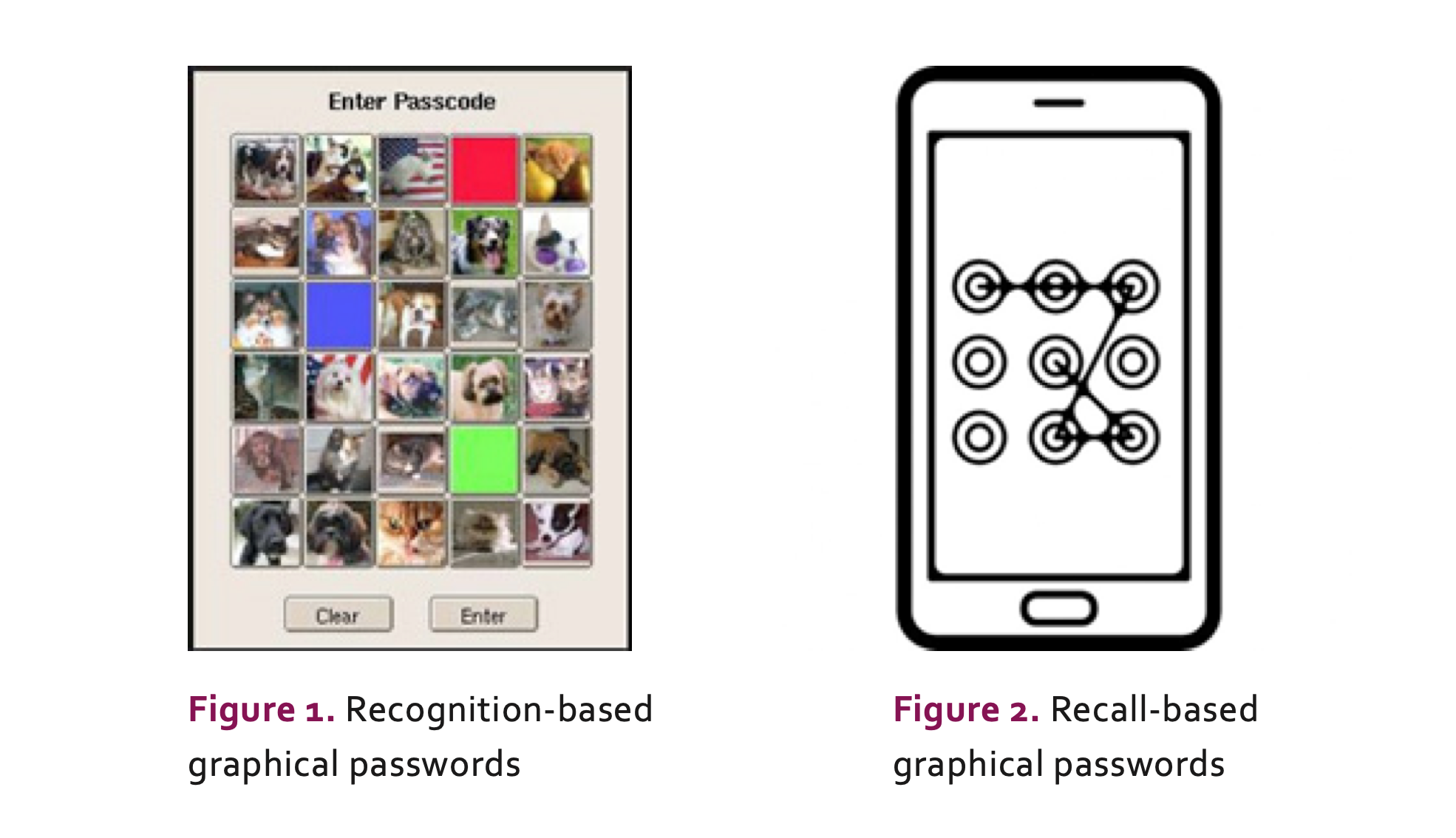
Graphical passwords can be categorized as those based on recognition and those that use the ability to recall. The first, similarly to text passwords, challenges the user to remember a number of images that they selected upon registration. The second asks them to reproduce something that they created during registration, such as
a pattern. Figures 1 and 2 show examples of recognition-based and recall-based graphical passwords, respectively.
Although graphical passwords alleviate text passwords memorability issues, they have the drawback that they are often easier to guess, as there are usually fewer possible password combinations in these methods. On the other hand, graphical passwords are easier to use on mobile devices than text passwords, as it is harder to input a string using a touch screen.
For more information on graphical passwords, the following articles can be read: Mihajlov and Jerman-Blažič (2011), Umar and Rafiq (2012), and Li et al. (2005).
Smart Cards
For this authentication method, a smart card is used to hold a user’s secret information, which is usually hard for them to remember. Smart cards are similar
to hardware tokens as they are required to be physically carried by the users. This provides stronger security than knowledge-based methods in the sense that a user must be holding the smart card in order to authenticate. One drawback is that, without it, not even the legitimate user can authenticate, forcing them to carry this smart card around. On the other hand, if the smart card is stolen, a thief can impersonate the user and gain access to their information for potentially malicious reasons.
Although there has been vast research on smart cards for remote authentication, they are best used on systems where users need to be physically present, as a reader is needed to interact with the smart card. As such, smart cards are often used for realizing payments.
For more information on smart cards, the following articles can be read: Tseng et al. (2008) and Cheng et al. (2012).
Mobile-Based Authentication
Through the years, mobile phones have become more and more like portable computers. Most people around the world possess at least one mobile device. Features like mobile-based authentication make the mobile phone an appealing device to use as a hardware token for authenticating users since it does not require them to hold additional tools.
There are multiple ways of using mobile phones as an authentication device. Two of the most common ways are the use of SMS and One Time Password (OTP) software. The first method relies on the mobile phones’ usage of text messages, also known as SMS, to send a code to the users’ phones for them to use to authenticate. The second method uses software installed on smartphones to generate random OTPs over time, in a similar manner as hardware tokens.
Mobile-based authentication is an interesting replacement to traditional software and hardware tokens, but it has its own issues as well. For example, the use of SMS is restricted by service providers and may not be received immediately. Just like any other possession-based method, if the mobile phone is lost or stolen, the user is unable to authenticate through it.
For more information on mobile-based authentication, the following articles can be read: Wu et al. (2004), Suoranta et al. (2012), Hallsteinsen and Jorstad (2007), and Alzomai et al. (2010).
Behavioral Biometrics
Behavioral biometrics are a sub-category among biometrics. These not only focus on recognizing the physical characteristics of a person, such as their face or fingerprints but their behavioral patterns as well. The following are some examples of behavioral biometrics:
-
Voice Biometrics: users are recognized based on their speech. This behavioral biometric is easy to implement as most modern computers and mobile devices possess a microphone
-
Keystroke Biometrics: users are recognized by analyzing their typing patterns. This can also be expanded to how users move the computer’s pointer or, for mobile devices, how users touch the screen
-
Risk-based Authentication: contextual and historical information of users is used to recognize changes in users’ behavior. This way, if a user tries to sign into an application through a different computer or network, they will be further prompted to authenticate
Although they are usually user-friendly, behavioral biometrics have the drawback that they are often easy to replicate. For example, in the case of voice biometrics, a recording of the user’s voice could be used by a third person to authenticate.
For more information on behavioral biometrics, the following articles can be read: Das et al. (2016), Traore et al. (2014), Krause (2014), and Wang et al. (2012).
Other Authentication Factors
Although the knowledge, possession, and inherence factors are well known, there are other factors that have been proposed. One of them is authentication through someone you know. Authentication methods in this factor base themselves on the relations users have with other users: if user A is friends with user B in the case of social networking sites.
For more information on this factor, the following article can be read: Brainard et al. (2006).
Another factor that has been proposed is that of “where you are,” which includes authentication methods based on the users’ geographic location. These methods make use of user-location gathering services, such as GPS, to validate that users are in the correct location for authenticating.
For more information on this factor, the following article can be read: Choi and Zage (2012).
Multi-Factor Authentication
As mentioned above, it is possible to combine two or more authentication methods belonging to different factors in order to increase an application’s security. This is known as multi-factor authentication. Any two or more authentication methods work for this, as long as they belong to different authentication factors. On the other hand, the combination of two or more authentication methods from the same factor is known as multi-modal authentication which, is often seen in biometrics but not the focus of this white paper.
Multi-factor authentication is more secure, as attackers have to break through all authentication methods in order to gain access to the legitimate user’s account. A drawback is that because users need to verify every authentication method, the authentication process takes longer.
For concrete examples of the different authentication method combinations, reference the following articles:
-
Combination of the Knowledge and Possession Factors: Yang et al. (2008) and Cao and Huang (2013)
-
Combination of the Knowledge and Inherence Factors: Kang et al. (2014) and Yu et al. (2008)
-
Combination of the Possession and Inherence Factors: Tang et al. (2013) and Clancy et al. (2003)
-
Combination of all three well-known factors: Zhang et al. (2015) and Yu et al. (2014)
Helping Developers With Their Decision-Making
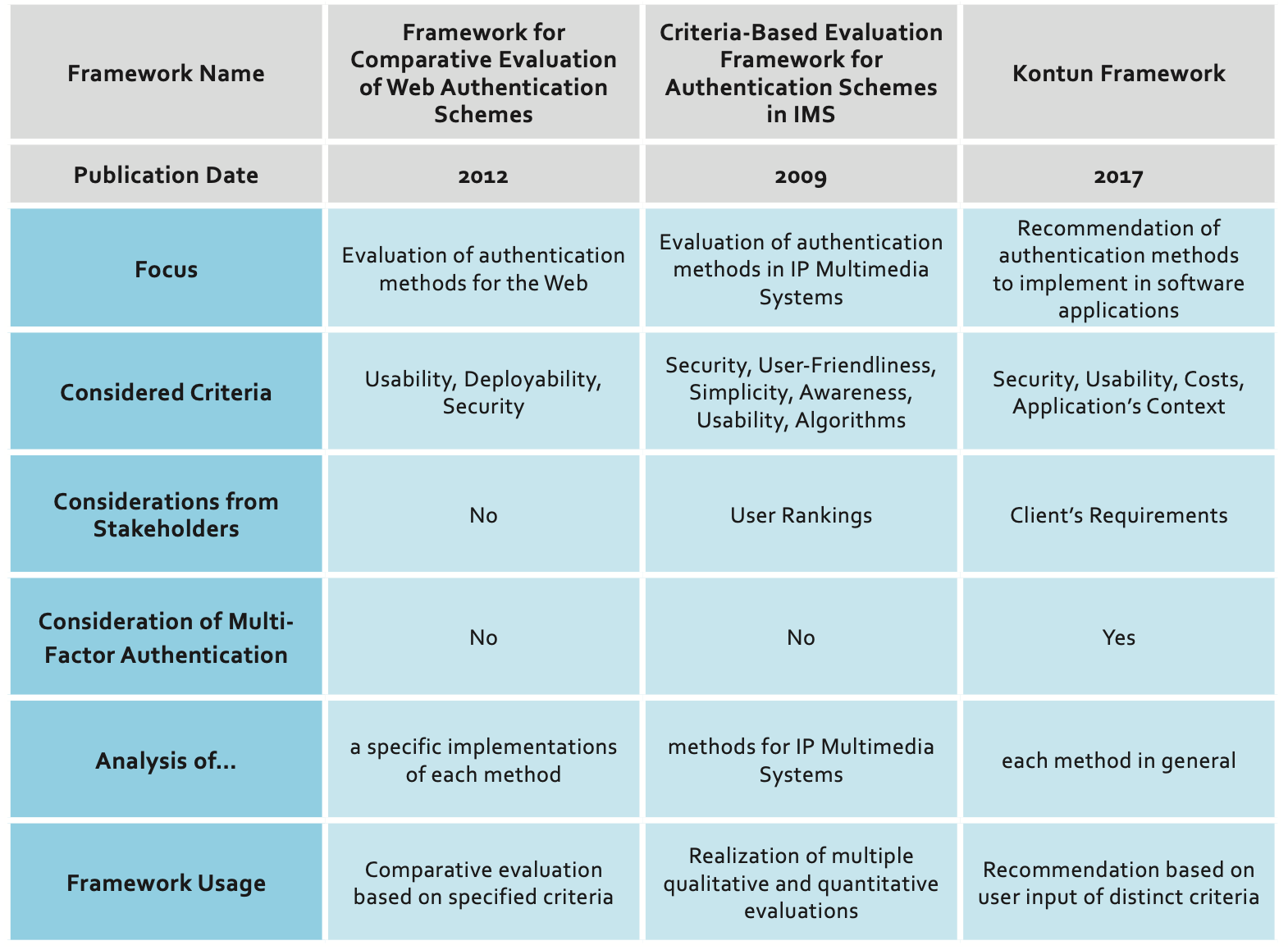
Existing frameworks help developers compare and select the best authentication methods for their needs. In this section, the strengths and weaknesses of the most relevant methods will be covered.
The Quest to Replace Passwords: A Framework for Comparative Evaluation of Web Authentication Schemes
This is an evaluation framework that helps analyze authentication methods with regard to their usability, deployability, and security benefits. Multiple attempts have been made to replace text passwords as the de-facto authentication method but none have managed to surpass them, especially in usability.
A detailed analysis of multiple authentication methods was performed in order to determine if they failed to offer or completely or partially offered the same levels
of usability, deployability, and security. Although this framework adequately covers authentication methods, it does not go into depth on multi-factor authentication. Moreover, the framework evaluated selected implementations of each authentication method and not each method as a whole. Regardless, every analysis is detailed enough to allow developers to comfortably compare and select the best authentication method for their needs.
For more information regarding this framework, please reference Bonneau et al. (2012).
A Criteria-Based Evaluation Framework for Authentication Schemes in IMS
This is an evaluation framework that aims to analyze authentication methods in IP Multimedia Systems (IMS). In order to accomplish this, three primary criteria are considered: security, user-friendliness, and simplicity. Three secondary criteria are considered as well: awareness, usability, and algorithms. Distinct qualitative and quantitative evaluations such as ISO guidelines and rankings from real users are performed on authentication methods based on these criteria.
Similar to the previous framework, this is only aimed at single-factor authentication methods. Only the framework for performing the evaluations is proposed, but no evaluation is performed.
For more information regarding this framework, the following article can be read: Eliasson et al. (2009) .
Kontun: A Framework for the Recommendation of Authentication Schemes and Methods
Nisum has been working in collaboration with the University of Bío-Bío on the creation of a recommendation framework that helps compare and select authentication methods.
This framework is called Kontun, which means “to enter a foreign property” as this is what authentication aims to prevent. It is in Mapudungun, the language spoken by Chile’s indigenous people.
The Kontun framework considers criteria related to security, usability, and costs. This enables them to recommend the most adequate single-factor and/or multi-factor authentication methods for the requirements given by the client.
A tool prototype has been developed to assist software developers using the Kontun framework. This prototype provides software developers with the option to configure the weights assigned to every criteria and context considered by the framework, in order to ensure the strongest authentication selection.
Unlike the previous frameworks, the Kontun framework considers multi-factor authentication and gives concrete answers for every software application based on its features.
There are three main steps for the Kontun framework‘s utilization:
-
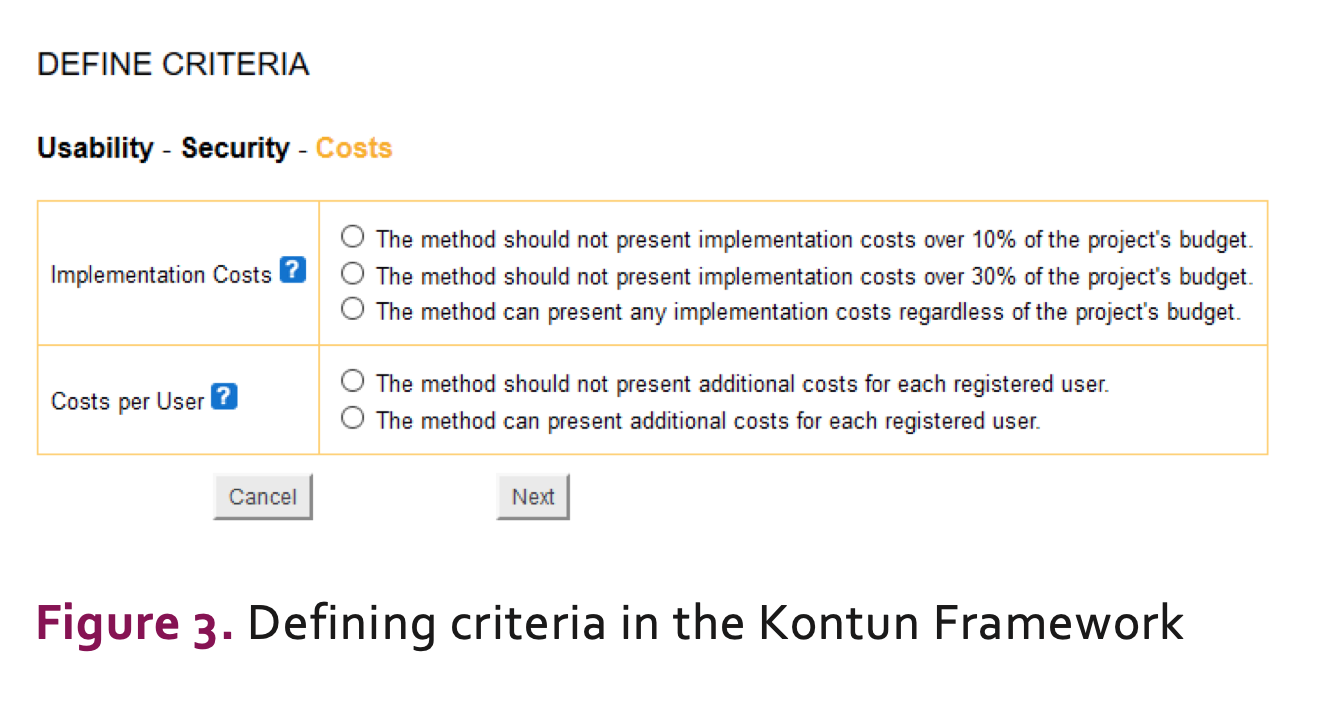
Criteria Definition: the software development team’s representative (SDTR) selects an importance level for every criterion considered by the framework. These importance levels are based on the priority that should be given to each criterion for the current application that is being analyzed. Figure 3 shows a screenshot from the tool prototype of the cost-related criteria and their corresponding importance levels.
-
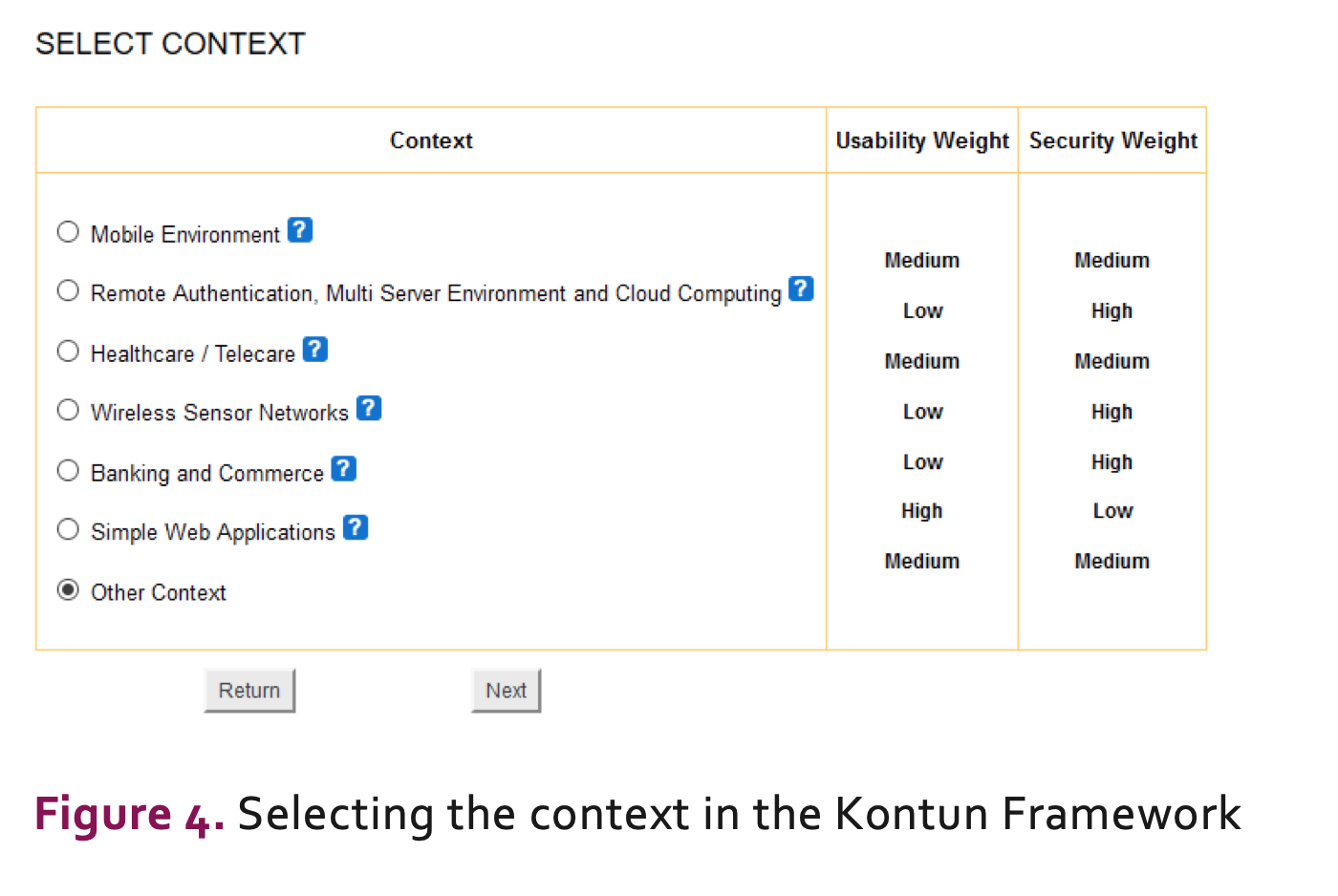
Context Selection: from the list of contexts the framework considers, the SDTR chooses the most appropriate application context for the current problem. If no context is adequate, a default option of “other context” is available as well. Figure 4 shows a screenshot from the tool prototype of the contexts considered by the framework.
-
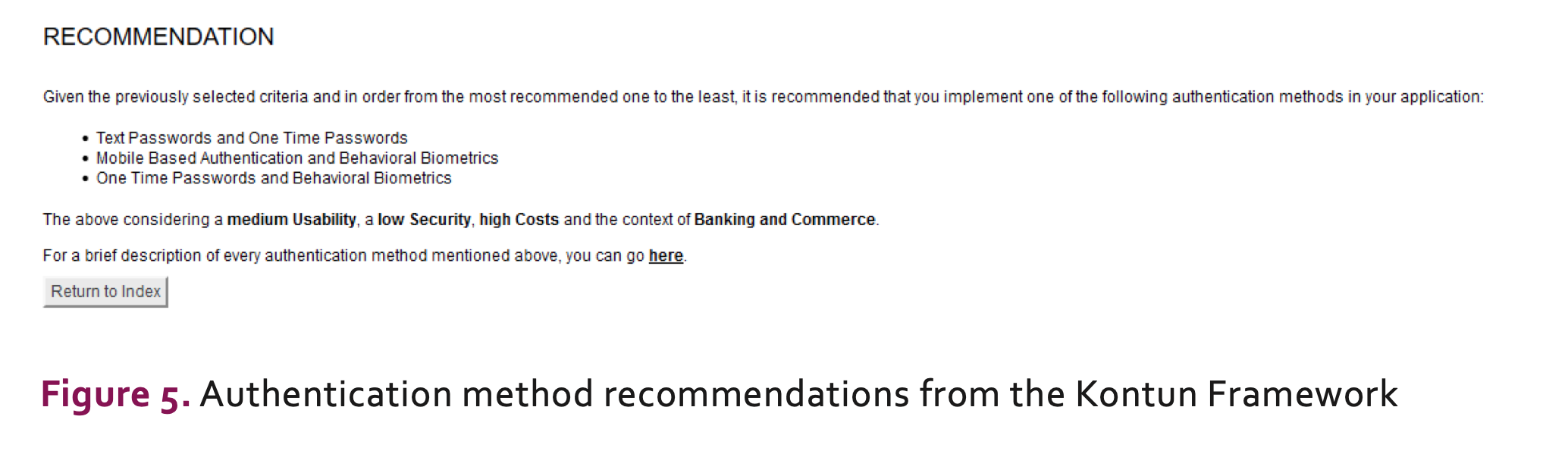
Framework’s Recommendation: Finally, based on both the defined criteria and the selected context, the Kontun framework recommends the strongest aligned single-factor and/or multi-factor authentication methods for the application being considered by the SDTR. An example of this can be observed in Figure 5.
The tool prototype can be obtained from this link: http://colvin.chillan.ubiobio.cl/mcaro/
Comparison of the Different Frameworks
Following is a comparison table to highlight the pros and cons of each of the frameworks just discussed (Table 1 ).
Table 1. Comparison of the different frameworks’ features
Conclusions
We included brief reviews of the three most well-known, as well as several lesser-known authentication methods. Single- and multi-factor authentications were reviewed as well.
Referencing the chart above, it can be deduced that there are no perfect authentication methods but each has its strengths and weaknesses. It is important to identify what is needed of the authentication method in order to determine which is best to implement in any given case. Kontun is an authentication tool and is available to help you make the best selection of authentication schemes.
With this white paper, Nisum along with the University of Bío-Bío aims to highlight concerns with authentication. The Kontun framework has been created with the hopes of complementing other frameworks that assist in the comparison and selection of authentication methods.
Acknowledgments
The following people participated in the creation of the Kontun Framework:
-
Coordinator: Renato San Martín B.
-
Expert Panel that helped to validate the Framework: Germán González, Sai Krishna, Lino Hernandez, José Flores, Ender Vargas, Christian Wells.
-
Other Collaborations: Mohammed Faraz, Krishna Rangavajhala.
-
Collaborators from the University of Bío-Bío: Ignacio Velásquez, Angélica Caro, Alfonso Rodríguez.
-
Everyone who participated during the surveys, interviews, and case studies performed to gather information and to validate the Framework’s recommendations respectively.
References
Alzomai, M ., Alfayyadh, B ., Jøsang, A .: Display security for online transactions: SMS-based authentication scheme. In: 2010 International Conference for Internet Technology and Secured Transactions, ICITST 2010. (2010)
Bonneau, J ., Herley, C ., Van Oorschot, P .C., Stajano, F .: The quest to replace passwords: A framework for comparative evaluation of web authentication schemes. In: 2012 IEEE Symposium on Security and Privacy, pp. 553-567. IEEE, (2012)
Brainard, J., Juels, A., Rivest, R.L., Szydlo, M., Yung, M .: Fourth-factor authentication: somebody you know. Proceedings of the 13th ACM conference on Computer and communications security. ACM, Alexandria, Virginia, USA (2006)
Cao, T ., Huang, S .: Two-factor authentication schemes based smart card and password with user anonymity. Journal of Computational Information Systems 9, 8831- 8838 (2013)
Cheng, Z.Y., Liu, Y., Chang, C.C., Chang, S.C.: A smart card based authentication scheme for remote user login and verification. International Journal of Innovative Computing, Information and Control 8, 5499-5511 (2012)
Choi, S ., Zage, D .: Addressing insider threat
using “where you are” as fourth factor authentication. In: Security Technology (ICCST), 2012 IEEE International Carnahan Conference on, pp . 147-153. (2012)
Clancy, T.C., Kiyavash, N., Lin, D.J.: Secure smartcardbased fingerprint authentication. Proceedings of the 2003 ACM SIGMM workshop on Biometrics methods and applications. ACM, Berkley, California (2003)
Das, R .K ., Jelil, S ., Mahadeva Prasanna, S .R .: Development of Multi-Level Speech based Person Authentication System. Journal of Signal Processing Systems 1-13 (2016)



